Access Key Configuration
EnterpriseBacula Enterprise Only
This solution is only available for Bacula Enterprise. For subscription inquiries, please reach out to sales@baculasystems.com.
The utilization of Bacula Enterprise Amazon RDS Plugin requires the involvement of an AWS IAM service user who possesses a specific set of permissions outlined below.
Subsequently, the user must establish an access key, which should be configured as Fileset parameters. This configuration enables the plugin to effectively retrieve or write data during backup or restore operations.
The plugin needs the following set of permissions to work appropriately:
Full RDS service permissions for the target instances or clusters
Full S3 service permissions or permissions to fully manage the destination bucket to be used for the export operation, enabling snapshots to be exported to it and allowing data to be retrieved and sent to the SD
The user needs to be associated with an export role that needs to be created beforehand (refer to the details below)
The user needs to have decrypt permissions using a KMS Service Key that needs to be created in advance (refer to the details below)
As an example, the final set of permissions of the user should resemble the image provided below:
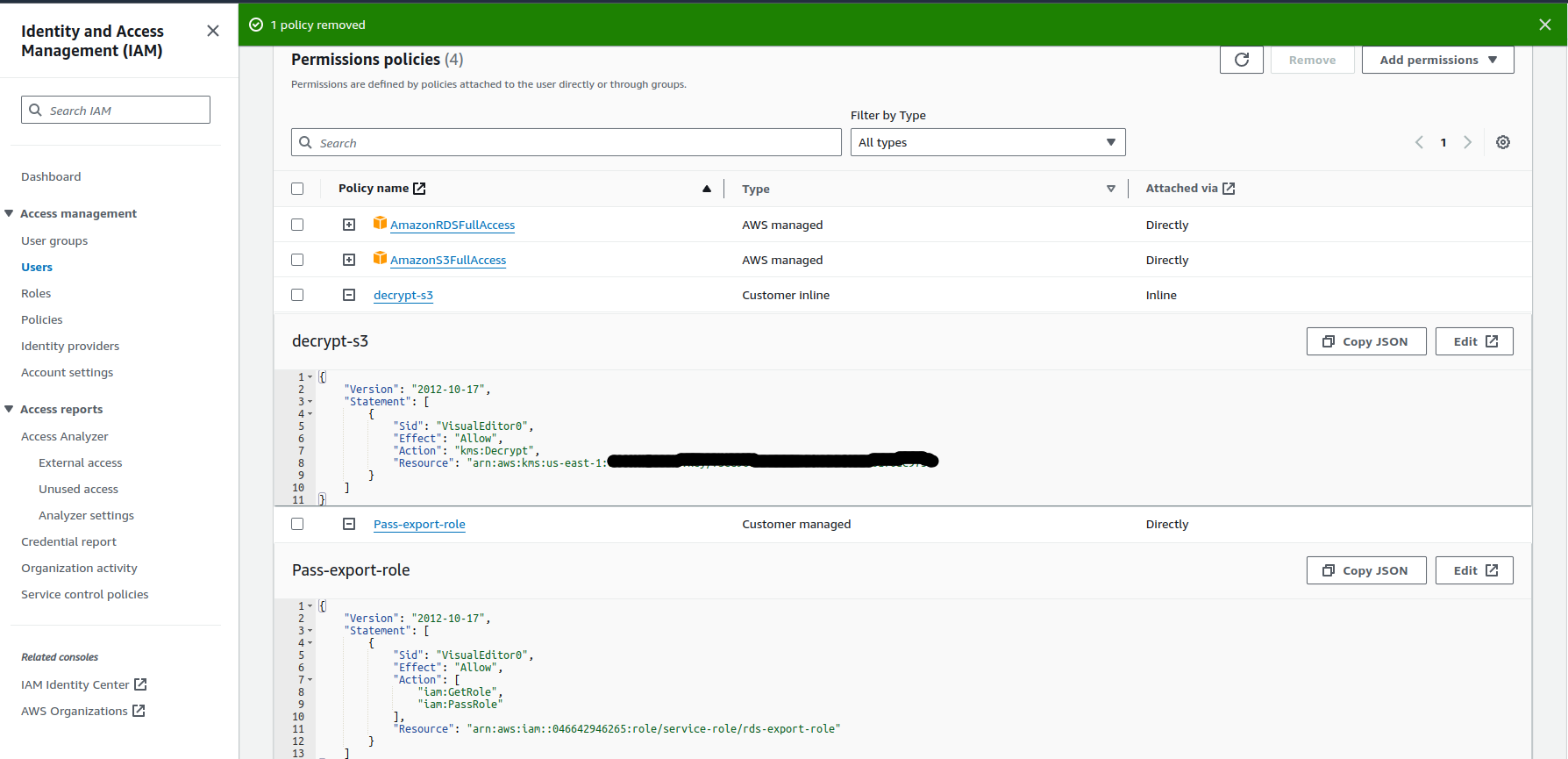
RDS Permissions Summary for the user
Note that for export operations to succeed, all of the following parameters must be defined: export_bucket, export_role, export_key, access_key, secret_key.
Export Role
It is necessary to grant tasks write-access permission for the snapshot export tasks to the Amazon S3 bucket designated for exporting the backups. This can be accomplished in 3 steps with a user with permissions to manage policies and roles within the IAM service:
# 1. Create a policy using the proper bucket name instead of EXAMPLE-BUCKET
$ aws iam create-policy --policy-name ExportPolicy --policy-document '{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "ExportPolicy",
"Effect": "Allow",
"Action": [
"s3:PutObject*",
"s3:ListBucket",
"s3:GetObject*",
"s3:DeleteObject*",
"s3:GetBucketLocation"
],
"Resource": [
"arn:aws:s3:::EXAMPLE-BUCKET",
"arn:aws:s3:::EXAMPLE-BUCKET/*"
]
}
]
}'
# 2. Create a IAM role, so that Amazon RDS can assume this IAM role on your behalf to access your Amazon S3 buckets.
aws iam create-role --role-name rds-s3-export-role --assume-role-policy-document '{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "export.rds.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}'
# 3. Attach the IAM policy to the just created role
aws iam attach-role-policy --policy-arn your-policy-arn --role-name rds-s3-export-role
# 4. In the User Management screen, associate the created role to the user that will contain the access key for Bacula Enterprise Amazon RDS Plugin
For more information, consult: https://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/USER_ExportSnapshot.html#USER_ExportSnapshot.SetupIAMRole
Encryption Key
Create a symmetric encryption AWS KMS key for the server-side encryption. The KMS key is used by the snapshot export task to set up AWS KMS server-side encryption when writing the export data to S3.
The KMS key policy must include both the kms:CreateGrant and kms:DescribeKey permissions. For more information on using KMS keys in Amazon RDS, visit AWS KMS key management official documentation.
Below is an example of a KMS-created key along with its policy.
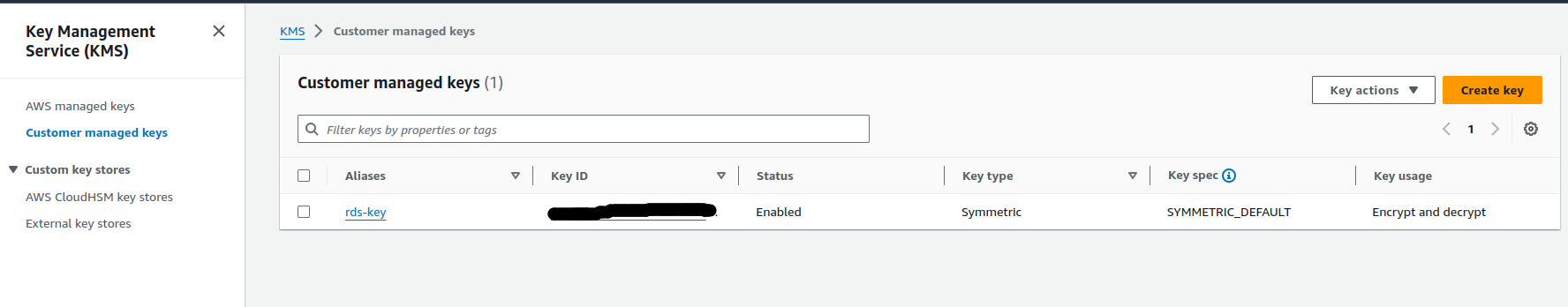
KMS Key
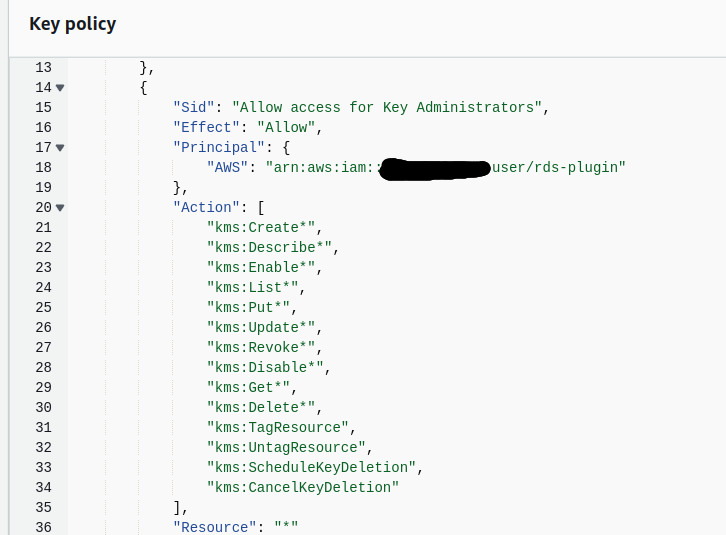
KMS Key Policy
After creating the key, the IAM user employed for the Amazon RDS Plugin needs to reference the key with a policy similar to what was shown before, using the proper ARN. Below, the policy example from it:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": "kms:Decrypt",
"Resource": "arn:aws:kms:us-east-1:046642946265:key/xxxxxxx-yyyy-zzzz-aaaa-bbbbbbbbbbbbbbb"
}
]
}
Access Key
After the user has been set up, it is essential to navigate to access keys and generate a new one:
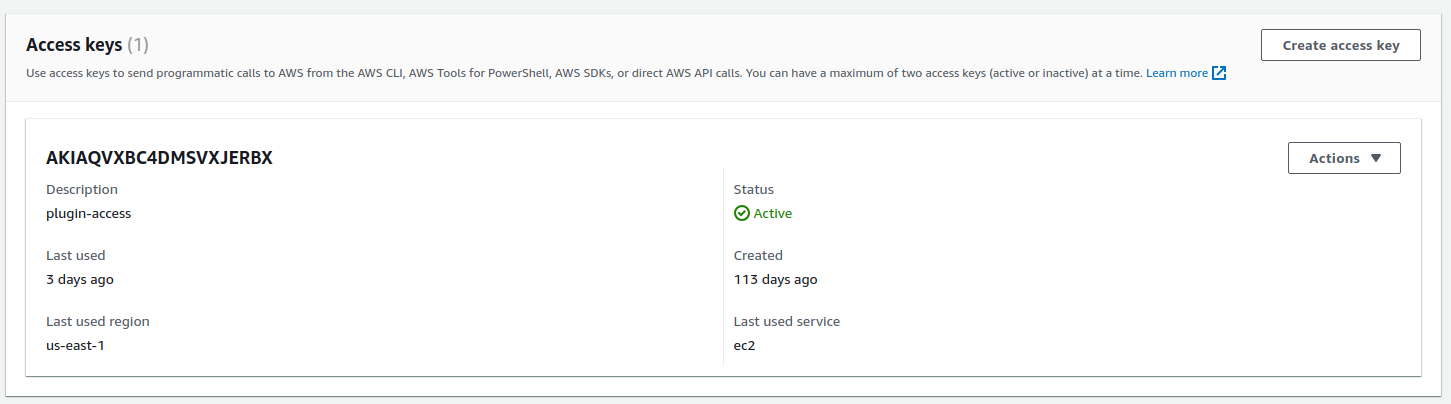
Amazon RDS Access Key
The Id of the key and the associated secret are the parameters
to configure in the plugin Fileset in access_key and access_secret parameters.
Adding also the region parameter should be enough to allow the plugin to connect
to the target dataset to protect.
See also
Go to Fileset Configuration
Go back to: Configuration.