Management of Profiles and Users
To access user management found in Configuration \(\rightarrow\)
Users (see figures 24 and 25), you must active
the security function in the general BWeb configuration (see the section
Self User Restore). Note, if you activate the security function without
having configured Lighttpd authentication, you will not be able to
access BWeb. In such a case, you must manually deactivate the security
feature by modifying the file /opt/bweb/etc/bweb.conf.
To activate access control by user profile, check the security_acl
option in the general BWeb configuration.
By default in BWeb the user admin has full privileges that cannot be
disabled. If you experience configuration problems, you can use the
admin account to reconfigure BWeb.
Figure 24: Users management
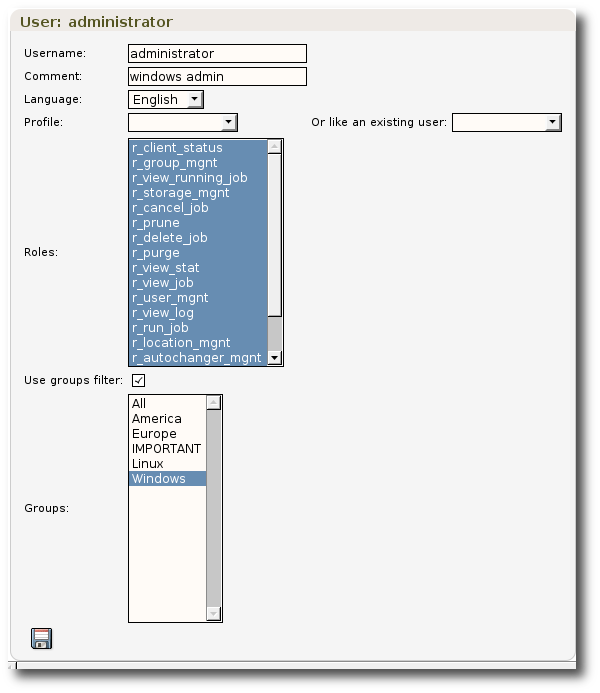
Figure 25: User configuration
Restrict Bacula Resources
The bconsole BWeb configuration option can use %u to specify a
specific bconsole configuration file. Then, it is possible to use
restricted Consoles and fine tune permissions for BWeb. Note that in
this case, it is mandatory to create a bconsole configuration file
for the default admin user.
bconsole = /opt/bacula/bin/bconsole -n -c /opt/bacula/etc/bconsole-%u.conf
# cat /opt/bacula/etc/bconsole-admin.conf
Director {
Name = "ks82-dir"
Address = "ks82"
DirPort = 9101
Password = "bacula"
}
# cat /opt/bacula/etc/bconsole-user1.conf
Director {
Name = "ks82-dir"
Address = "ks82"
DirPort = 9101
Password = "bacula"
}
Console {
Name = user1
Password = "bacula"
Director = "ks82-dir"
}
# cat /opt/bacula/etc/bacula-dir.conf
Console {
Name = "user1"
CatalogAcl = *all*
ClientAcl = aclient-fd, otherclient-fd
CommandAcl = *all*
FilesetAcl = *all*
JobAcl = home,usr
Password = "bacula"
PoolAcl = *all*
ScheduleAcl = *all*
StorageAcl = *all*
WhereAcl = *all*
DirectoryAcl = *all*
UserIdAcl = *all*
}
User Password Management
The following lighttpd configuration permits limiting access with
basic authentication. After changing the lighttpd config file, you need
to restart the bweb service:
# more /opt/bweb/etc/httpd.conf
...
server.modules += ( "mod_auth") # if not already done
auth.backend = "htpasswd"
auth.backend.htpasswd.userfile = "/opt/bweb/etc/htpasswd.bweb"
auth.require = ( "/" =>
(
"method" => "basic",
"realm" => "Password protected area",
"require" => "valid-user"
)
)
...
The command htpasswd enables you to manage the list of users that
can authenticate.
# htpasswd -c /opt/bweb/etc/htpasswd.bweb admin
New password:
Re-type new password:
Adding password for user admin
Note
To add more users using the htpasswd command, you should remove the -c option:
# htpasswd /opt/bweb/etc/htpasswd.bweb demouser
When creating Lighttpd authentication, the user names given must
correspond to the user names configured in BWeb. For example if your
LDAP user name is admin-windows, the BWeb user name you
configured must also be admin-windows.
See Security Access for more information about user password management.
Note, if you use the basic authentication and you are going to register
new Bacula Clients by using QR code or registration link, you need to
uncomment in lighttpd configuration the following two lines:
## Uncomment this line if you use client registration by QR code or registration link
#$HTTP["url"] !~ "^/cgi-bin/bweb/register.pl$" {
## Uncomment this line if you use client registration by QR code or registration link
#}
This way users, who register clients by QR code or registration link, will not be asked about login/password.
System Auth
The option System authentication 1 enables BWeb to authenticate
users with the PAM subsystem via the su command. With the
System Authentication option, only users defined on the Bacula
Linux/Unix server will be allowed to use BWeb. With this option, if a
user “admin” is defined on the system, it will be mapped automatically
to the BWeb “admin” special account.
Permissions
Permission |
Description |
|---|---|
|
This permission is required to use the user management screen to view or modify users permissions. |
|
The permission is required for management of Bacula client groups. |
|
All configure screens require this permission. The Bacula configuration part of BWeb requires this permission. |
|
Management of autochangers requires this permission. |
|
Screens managing adding or modification of Volume locations require this permission. |
|
Media management is required to update the media properties and load/unload media. |
|
Screens managing adding or modification of storage and devices require this permission. |
|
If this permission is set, you can prohibit or authorize Job and Job history deletion. |
|
Required to achieve the |
|
Required to achieve the |
|
This permission allows the user to view jobs. |
|
This permission allows the user to view the job logs. |
|
Required to view the media. |
|
Required to display the statistics. |
|
Required to view the groups. |
|
This permission is required to be able to follow real-time Job execution. |
|
This permission is required to start Jobs via BWeb. |
|
This permission is required to start restore Jobs via BWeb. |
|
This permission is required to restart Jobs that were stopped or failed into an incomplete state. |
|
This permission is required to prohibit or authorize Job cancellation. |
|
This permission allows the user to obtain the client status. |
|
This permission enables to stop the Job. |
|
This permission enables to cancel the Job. |
|
This permission allows the client bandwidth limit setting. |
|
Required to run the bconsole commands via the web bconsole. |
Self User Restore
The option Self User Restore 2, used in conjunction with the
Security or the System authentication options, enables BWeb to
display a restricted view to users who are not defined in the BWeb
system.
For example, If a Linux/Unix user called “john” is logged on his Linux/Unix workstation “john-laptop” and he points his FireFox web browser to BWeb, once logged into the BWeb system as “john”, BWeb will search in the Bacula Director Client list for a system that matches the IP address of the workstation connected (probably “john-laptop-fd” in this case) and will restrict the restore process to this particular client automatically. If the Unix user information for “john” is available via the getpwnam() system interface, the restore process will automatically limit the files that can be viewed and restored to the files that the Unix user “john” can normally see or access.
The IP of the workstation can be found in the BWeb access log configured
in lighttpd (/opt/bacula/working/bweb-access.log).
In addition, it is possible to use other Console ACLs such as
DirectoryAcl or WhereAcl to apply even more access restrictions.
On Windows clients, it is not possible to automatically limit what a
user can see. Here, the DirectoryACL directive must be used to limit
the view and the restore capabilities of the user.
See also
Go back to:
Go back to the BWeb Configuration chapter.
Go back to the Bweb Management Suite chapter.
Go back to the Bacula Enterprise User Interfaces.